| Original author(s) | David Woodhouse |
|---|---|
| Developer(s) | Daniel Lenski, Nikos Mavrogiannopoulos |
| Initial release | March 18, 2009[1] |
| Stable release | |
| Repository | |
| Type | VPN |
| License | GNU LGPL v2.1[2] |
| Website | www.infradead.org/openconnect/ |
Cisco Anyconnect Open Source Client
- Compare Cisco AnyConnect alternatives for your business or organization using the curated list below. SourceForge ranks the best alternatives to Cisco AnyConnect in 2021. Compare features, ratings, user reviews, pricing, and more from Cisco AnyConnect competitors and alternatives in order to make an informed decision for your business.
- A vulnerability in the interprocess communication (IPC) channel of Cisco AnyConnect Secure Mobility Client Software could allow an authenticated, local attacker to cause a targeted AnyConnect user to execute a malicious script. The vulnerability is due to a lack of authentication to the IPC listener. An attacker could exploit this vulnerability by sending crafted IPC messages to the AnyConnect.
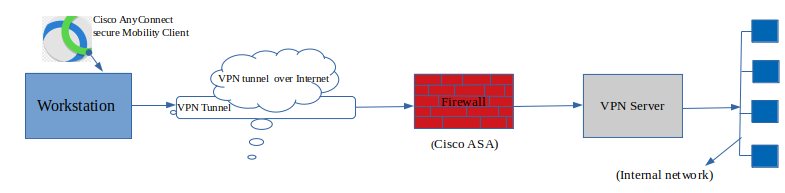
OpenConnect is an open-source software application for connecting to virtual private networks (VPN), which implement secure point-to-point connections.
It was originally written as an open-source replacement for Cisco's proprietaryAnyConnect SSL VPN client,[3] which is supported by several Cisco routers.The OpenConnect client added support for Juniper Networks' SSL VPN in version 7.05,.[1] A fork then developed support for Palo Alto Networks' GlobalProtect VPN,[4] which was included in the version 8.00 release.[5]
2 factor Authentication SSL VPN - Anyconnect ( help ) Hi, Kindly advice any software vendor to provide dual authentication using Phone as secondary auth for my cisco anyconnect SSL. Currently using ASA version 8.0 (5) 25 ( not able to use Duo Security product ).
Server[edit]
As of 2013, the OpenConnect project also offers an AnyConnect-compatible server, ocserv,[6] and thus offers a full client-server VPN solution.
OpenConnect and ocserv now implement an extended version of the AnyConnect VPN protocol, which has been proposed as an Internet Standard.[7] Both OpenConnect and ocserv strive to maintain backwards-compatibility with Cisco AnyConnect servers and clients.

Protocols[edit]
Cisco Anyconnect Log In
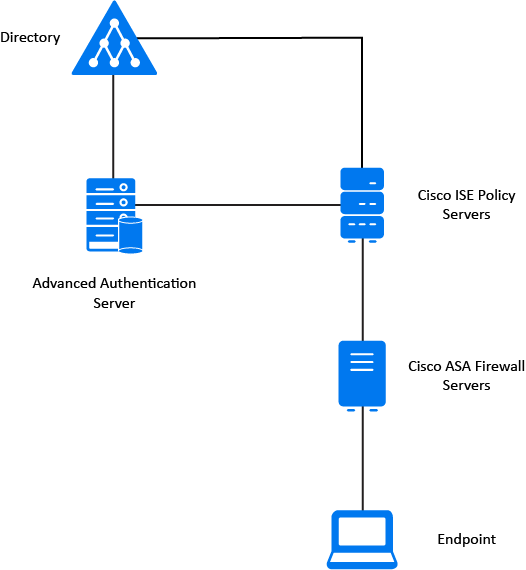
Cisco AnyConnect[edit]
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic,[8][9] and can fall back to TLS-based transport where firewalls block UDP-based traffic. The DTLS protocol used by Cisco AnyConnect servers was based on a non-standard, pre-release draft of DTLS 1.0, until support for the DTLS 1.2 standard was added in 2018.[9][10]
OpenConnect's implementation of the AnyConnect protocol is sufficiently complete that some of Cisco's own IP phone devices embed a very old release of OpenConnect[11] (rather than Cisco's own proprietary software) in order to be able to connect to Cisco SSL VPNs.[12][13]
DTLS[edit]
Cisco's proprietary AnyConnect clients and servers were originally built against a patched, 2007 release of OpenSSL 0.9.8f,[14] which implemented a pre-release version of DTLS that was not compatible with DTLS 1.0 as standardized in RFC 4347. Because of this, it was difficult to make OpenConnect implement a Cisco-compatible version of DTLS without linking against OpenSSL.
Explicit support for Cisco's non-standard version of DTLS was included in OpenSSL 0.9.8m (where it is known as DTLS1_BAD_VER) and then GnuTLS 3.2.1 (where it is known as GNUTLS_DTLS0_9).[15] Newer versions of Cisco's AnyConnect clients and servers support DTLS 1.2 in its standardized on-the-wire form (RFC 6347), though they continue to use a non-standard mechanism (based on session resumption) for DTLS key exchange.[7]
Modern versions of OpenConnect can be built to use either the GnuTLS or OpenSSL for TLS, DTLS, and cryptographic primitives.
Other protocols[edit]
The OpenConnect client also implements Juniper, Junos Pulse, and GlobalProtect VPN protocols. These have a very similar structure to the AnyConnect protocol: they authenticate and configure routing over TLS, except that they use ESP for efficient, encrypted transport of tunneled traffic (instead of DTLS), but they too can fall back to TLS-based transport.As of May 2020, support for several PPP-based protocols is in development.[16]
Architecture[edit]
The OpenConnect client is written primarily in C, and it contains much of the infrastructure necessary to add additional VPN protocols operating in a similar flow, and to connect to them via a common user interface:[17]
- Initial connection to the VPN server via TLS
- Authentication phase via HTTPS (using HTML forms, client certificates, XML, etc.)
- Server-provided routing configuration, in a protocol-agnostic format, which can be processed by a vpnc-script
- Data transport phase via a UDP-based tunnel (DTLS or ESP), with fallback to a TLS-based tunnel
- Built-in event loop to handle Dead Peer Detection, keepalive, rekeying, etc.
OpenConnect can be built to use either the GnuTLS or OpenSSL libraries for TLS, DTLS and cryptographic primitives.
Platforms[edit]
OpenConnect is available on Solaris, Linux, OpenBSD, FreeBSD, MacOS, and has graphical user interface clients for Windows,[18]GNOME,[19] and KDE.[20] A graphical client for OpenConnect is also available for Android devices,[21]and it has been integrated into router firmware packages such as OpenWrt.[22]
References[edit]
- ^ abcinfradead.org - OpenConnect: Changelog.
- ^gitlab.com - OpenConnect: License.
- ^''Development of OpenConnect was started after a trial of the Cisco client under Linux found it to have many deficiencies …''. Infradead.org. Retrieved 2018-08-13.
- ^dlenski/openconnect on GitHub
- ^'OpenConnect 8.00 release'. Lists.infradead.org. Retrieved 2019-01-05.
- ^ocserv home page.
- ^ abN. Mavrogiannopoulos (October 2018). The OpenConnect VPN Protocol Version 1.1. IETF. I-D draft-mavrogiannopoulos-openconnect-02.
- ^Tiso, John; Scholfield, Mark D.; Teare, Diane (2011). Designing Cisco Network Service Architectures (ARCH): Foundation Learning Guide. Foundation Learning Guides (3 ed.). Cisco Press. p. 464. ISBN9781587142888. Retrieved 2013-06-13.
Cisco AnyConnect is a Cisco implementation of the thick client. Because the SSL VPN network extension runs on top of the SSL protocol, it is simpler to manage and has greater robustness with different network topologies such as firewalls and Network Address Translation (NAT) than the higher security of IPsec.
- ^ abMavrogiannopoulos, Nikos (2013-11-17). 'nmav's Blog: Inside an SSL VPN protocol'. Nmav.gnutls.org. Retrieved 2018-08-13.
- ^'Release Notes for the Cisco ASA Series, 9.10(x)'. Cisco. December 12, 2018.
- ^'ocserv issues #51'.
- ^Nikos Mavrogiannopoulos. 'Recipe: VoIP network with ocserv'.
- ^'Open Source License Notices for the SPA525G'(PDF). Cisco.
- ^David Woodhouse (September 23, 2008). 'DTLS clue requested'.
- ^David Woodhouse. 'How the VPN works § DTLS compatibility'.
- ^https://gitlab.com/openconnect/openconnect/-/issues?label_name%5B%5D=PPP
- ^Daniel Lenski (September 17, 2020). 'How VPNs Work- The Ins and Outs'. DAMA Portland.
- ^'Openconnect graphical client'. GitHub. Retrieved 2014-10-28.
- ^'NetworkManager-openconnect'. gnome.org. Retrieved 2020-01-27.
- ^'NetworkManagement'. kde.org. Retrieved 2014-10-28.
- ^cernekee. 'Android UI for OpenConnect VPN client'. GitHub. Retrieved 2014-10-28.
- ^'VPN Overview'. openwrt.org. Retrieved 2018-03-15.
External links[edit]
Some useful usage information.
Overview
Stanford's VPN allows you to connect to Stanford's network as if you were on campus, making access to restricted services possible. To connect to the VPN from your Windows computer you need to install the Cisco AnyConnect VPN client.
Two types of VPN are available:
- Default Stanford (split-tunnel). When using Stanford's VPN from home, we generally recommend using the Default Stanford split-tunnel VPN. This routes and encrypts all traffic going to Stanford sites and systems through the Stanford network as if you were on campus. All non-Stanford traffic proceeds to its destination directly.
- Full Traffic (non-split-tunnel). This encrypts all internet traffic from your computer but may inadvertently block you from using resources on your local network, such as a networked printer at home. If you are traveling or using wi-fi in an untrusted location like a coffee shop or hotel, you may wish to encrypt all of your internet traffic through the Full Traffic non-split-tunnel VPN to provide an additional layer of security.
Open Source Fnaf
You can select the type of VPN you want to use each time you connect to the Stanford Public VPN.
Install the VPN client
- Download the Cisco AnyConnect VPN for Windows installer.
- Double-click the InstallAnyConnect.exe file.
- When a message saying the Cisco AnyConnect client has been installed, click OK.
Connect to the Stanford VPN
- Launch the Cisco AnyConnect Secure Mobility Client client.
If you don't see Cisco AnyConnect Secure Mobility Client in the list of programs, navigate to Cisco > Cisco AnyConnect Secure Mobility Client. - When prompted for a VPN, enter su-vpn.stanford.edu and then click Connect.
- Enter the following information and then click OK:
- Group: select Default Stanford split- tunnel (non-Stanford traffic flows normally on an unencrypted internet connection) or Full Traffic non-split-tunnel (all internet traffic flows through the VPN connection)
- Username: your SUNet ID
- Password: your SUNet ID password
- Next, the prompt for two-step authentication displays. Enter a passcode or enter the number that corresponds to another option(in this example, enter 1 to authenticate using Duo Push to an iPad). Then click Continue.
- You may have to scroll down the list to see all of your options.
- If your only registered authentication method is printed list, hardware token, or Google Authenticator, the menu does not display. Enter a passcode in the Answer field and click Continue.
- Click Accept to connect to the Stanford Public VPN service.
- Once the VPN connection is established, a message displays in the lower-right corner of your screen, informing you that you are now connected to the VPN.
Disconnect from the Stanford VPN
- In the notification area, click the Cisco AnyConnect icon if it is displayed. Otherwise, go to your list of programs and click Cisco AnyConnect Secure Mobility Client.
- At the prompt, click Disconnect.
